Mainframe Penetration Testing
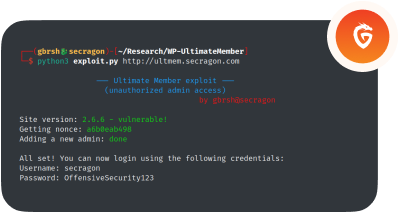
Our Mainframe Penetration Testing services evaluate the security of your mission-critical mainframe systems by identifying and addressing vulnerabilities that could be exploited by hackers. Safeguard your organization’s valuable data, maintain compliance with industry regulations, and strengthen your overall security posture by proactively addressing mainframe-specific risks.