Every Bit, Every Byte,
Where vulnerabilities exist attacks happen
Act Today, Secure Tomorrow!
Application Security
Identify vulnerabilities in consumer, commercial and industrial devices with a detailed security review from hardware to firmware (IoT, Medical Device, etc.)
Network Security
Identify vulnerabilities and exploits that threat actors could leverage to compromise your IT infrastructure and access sensitive data (Internal, External, WiFi, etc.)
Cloud Security
Review your configurations and replicate a targeted attack on your cloud environment to prevent unauthorized access (AWS, GCP, Azure, etc.)
TAILORED EXPERTISE
Cybersecurity Solutions by Industry
Find out how Secragon’s world-class cybersecurity services can
cater to the unique needs of your industry.
SECRAGON, YOUR CYBERSECURITY PROVIDER
We, at Secragon, are a team of certified ethical hackers, visionary security engineers, seasoned penetration testers, and committed project managers… but first of all – professionals, who LIVE and BREATHE Offensive Security. Along the list of qualifications, titles, and credentials, we bring a real “think outside of the box” mindset to every project and we constantly strive to learn, explore, and push forward to master complex concepts and deliver top-notch services and results.
Proven Methodologies & Standards
We are committed to delivering the highest quality and most consistent services using world-class methodologies and standards (OWASP, OSSTMM, MITRE ATT&CK, etc.)
- OWASP for Application Security
- MITRE ATT&CK Framework
- OSSTMM Open Source Security Testing Methodology
- PTES Penetration Testing Execution Standard

Cybersecurity Blog Articles
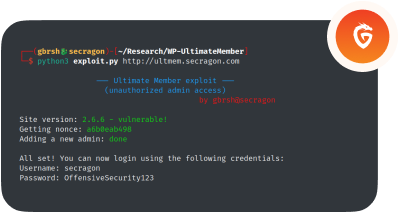
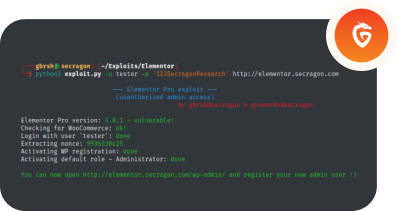
Discover the latest in cybersecurity, and our most recent CVEs,
vulnerabilities research and findings.